Question/Concern/Inquiry:
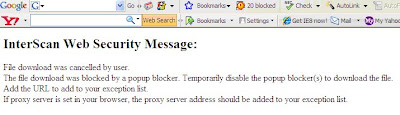
Based on your email, you had encountered an error while trying to download certain filev ia IWSVA.
I had check the screenshot that you had sent and found out that the error occured was caused by popup blocker. Most if the new browser had a built in popup blocker if you were going to look on your Browser the popup to download the file had been blocked.
To resolve this issue you can do the following;
1. Log in to your IWSVA.
2. Click HTTP>HTTP SCAN>Policies
3. At the right pane click the Virus Scan Global Policy 4. Click the Virus Scan Rule tab.
5. Under Large File Hnadling Choose Deffered Scanning.
6. Click Save.
Question:
Saril of NRE asked me on how to exclude mobile devices from assessment by Network Viruswall.
Answer:
To exclude smart phones/PDA from being assessed by Network Viruswall you can either;
1. Add in the smart phones/PDA IP address or MAC Address in the Global Exception List
2. Tick option to "Disable endpoint detection for non-windows Operating Systems" in the Network Viruswall console > Policy Enforcement > Policies.
Hope this helps.
Question/Concern/Inquiry:
Based on your message, you moved the NVWe and would like to re-deploy the PE agent. During uninstallation of PE Agent at vista machine, you encounter the following error whenever try to remove the PE Agent via Add/Remove Program .."..another installation is in progress.." If we try to use self installer i.e. peagent_config.exe we will receive the same error too.
Solution/Recommendation:
Please follow the steps below to manually uninstall the PE Agent to these machine:
1. On System Tray, right click PEAgent icon, then click "Uninstall Real-Time Scan".
2. Right click PEAgent icon, then click Exit.
3. Run command "\%WinDir%\PEAgent\PEAgent.exe /delete".
4. Delete the folder \%WinDir%\PEAgent.
 Untuk pendengar radio sonora yang terkasih, apakah anda ingin juga memasang sebuah widget streaming sehingga pengunjung anda juga dpt menikmati radio kesayangan masyarakat Jakarta terutama daerah2 yang tidak terjangkau oleh radio sonora. Nah, saya bisa membantu anda dengan menyediakan script yang membantu anda supaya bisa puter radio sonora FM di blogger. Sepotong script yang kecil dan pendek ini sangat membantu anda. Bisa kamu pasang dimanapun, di header blog, di sidebar blogger, di footer blogger dan dimanapun yang disukai. Banyak sekali berita-berita yang aktual dan informatif disediakan oleh radio ini karena afiliasinya dengan koran kompas, media yang paling terkenal di Indonesia.
Untuk pendengar radio sonora yang terkasih, apakah anda ingin juga memasang sebuah widget streaming sehingga pengunjung anda juga dpt menikmati radio kesayangan masyarakat Jakarta terutama daerah2 yang tidak terjangkau oleh radio sonora. Nah, saya bisa membantu anda dengan menyediakan script yang membantu anda supaya bisa puter radio sonora FM di blogger. Sepotong script yang kecil dan pendek ini sangat membantu anda. Bisa kamu pasang dimanapun, di header blog, di sidebar blogger, di footer blogger dan dimanapun yang disukai. Banyak sekali berita-berita yang aktual dan informatif disediakan oleh radio ini karena afiliasinya dengan koran kompas, media yang paling terkenal di Indonesia.
Apakah anda tertarik untuk puter radio di blogger?
Nih, ini scriptnya :
<embed src="http://radio.kompas.com/kradio/kompas.asx" autostart="false" width="200" height="28" volume="110" pluginspage="http://www.microsoft.com/Windows/Downloads/Contents/Products/MediaPlayer/"></embed>
NEW WORM_DOWNAD.E/Conficker Variant
04/09/2009
Details
This is a pro-active notification that Trend Micro received a new sample of DOWNAD and named it as WORM_DOWNAD.E Trend Micro has flagged this worm as noteworthy due to the increased potential for damage, and propagation. Including its ability to propagate via the Server service vulnerability.
Please visit Trend Micro’s DOWNAD Information page for the latest information:
http://us.trendmicro.com/us/threats/conficker-worm/
Arrival
This worm may be downloaded unknowingly by a user when visiting malicious Web sites.
This worm executes only after meeting any of the following trigger condition:
Any day before May 3, 2009
Propagation Routine
This worm propagates by taking advantage of a vulnerability discovered in certain Microsoft operating systems that could allow remote code execution if an affected system received a specially crafted RPC request, which also contains a shellcode.
This worm also attempts to propagate via the same vulnerability through the internet using external IP addresses by checking if the system is directly connected to the internet.
Other Details
This worm creates the temporary file in %System%/0{Random}.tmp which is a SYS file and is detected by Trend Micro as TROJ_DOWNAD.E. It then creates a service using this temporary file, thus the malicious routines of this malware are also exhibited in the system. After creating the service, the temporary file is deleted.
It then patches %System%\drivers\tcpip.sys in memory to modify the limitation of TCP maximum half-connection attempts number. After doing this, the created driver service is unloaded and deleted, leaving no trace in the registry.
It creates a thread that opens a random port to communicate with a remote computer. This worm also creates the following mutex “Global\{Random}” to ensure that only one instance of itself is running in memory:
_________________________________________________________________________________
Trend Micro Solutions
·VSAPI Pattern - Since OPR 5.953.00
·Intellitrap pattern - detected as PAK_Generic.001
·Damage Cleanup Template - DCT OPR 1026
_________________________________________________________________________________
DOWNAD/Conficker Best Practices
1. Patch Windows systems with the MS08-067
2. Verify OfficeScan Client Edition is up to date and proper sttings
http://esupport.trendmicro.com/pages/How-to-configure-Trend-Micro-products-for-best-protection-against-malw.aspx
3. Follow recommended solutions and protection
http://threatinfo.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=WORM%5FDOWNAD%2EE&VSect=Sn
_________________________________________________________________________________
Your concern as spoken over the phone as follows:
ServerProtect 5.58 installed on Windows 2003 server has problem to update with the latest component (scan engine and pattern file). It’s a fresh installation and you faced this problem since last week.
Information required:
Please forward to me tmudump.txt file (you can perform a search in C:\Program Files\Trend\Sprotect folder)
Screen shot of the error message (I’ve record down in text, however if I need to escalate this to Trend Support a screen shot will help)
Have you installed the latest patch for your ServerProtect 5.58? http://www.trendmicro.com/ftp/products/patches/spnt_558_win_en_patch7.exe
Screen shot of the update page screen. ( I want to see the current component version)
Please forward to me server.ini file from spntshare directory.
Feedback from customer:
She actually installed SPNT 5.7 on Windows 2003 32 bit. I asked her to remove SPNT 5.7 and install SPNT 5.58 instead. That solved the problem not able to update the scan engine and pattern file.
Another case is solved.
If you add spyware into the exclusion list, it will no longer detected as spyware the next time around. Until you remove the entry from SPYWAREEXCEPTIONLIST.INI by default located in your IWSS installation folder.
Do you want to check if you are infected with Conficker or Downad worm family? Verify from this test site Conficker Eye Chart
Blog Archive
-
▼
2009
(61)
-
▼
April
(9)
- Encountered an error while trying to download cert...
- Network Viruswall to exclude mobile device from as...
- Manually delete PEAgent for Network Viruswall
- Puter Radio Sonora Online di Blogger
- April Class
- [Trend Micro Advisory] NEW WORM_DOWNAD.E/Conficker...
- SPNT 5.7 is not for Windows 2003 server 32 bit
- Removing spyware from "exclusion list" in your IWSS
- very simple test that's available at the Conficker...
-
▼
April
(9)
